The Spinning Cube of Potential Doom
December 22, 2003
Contact: John Bashor, jbashor@lbl.gov, +1 510 486 5849
The Spinning Cube of Potential Doom visualizes passwords being sent "in the clear," that is, without encryption. These "cleartext" passwords can be easily intercepted, making them a security threat. (Image: Steve Lau)
At SC03 in Phoenix, many attendees passing the SCinet network operations center were curiously compelled to stop and watch “The Spinning Cube of Potential Doom,” the brainchild of Steve Lau, staff member at the National Energy Research Scientific Computing Center (NERSC).
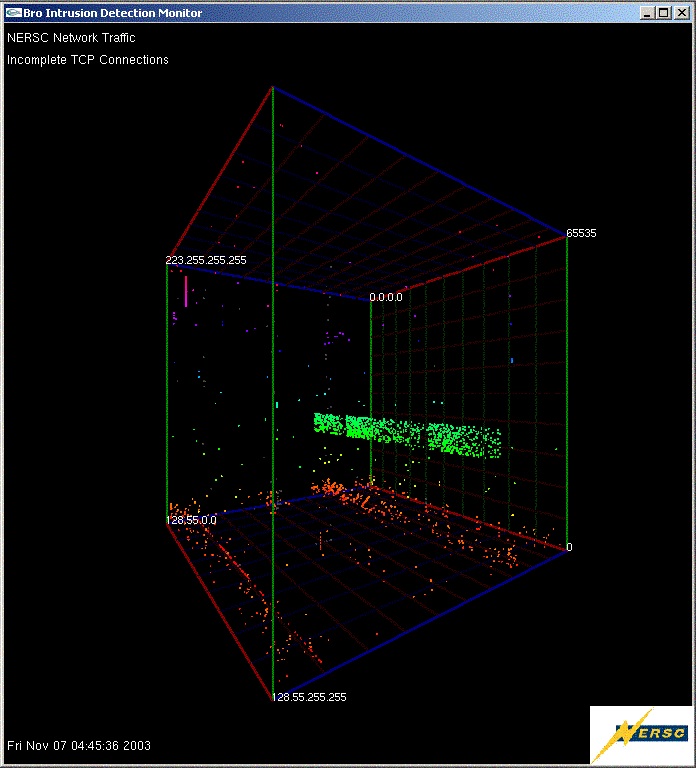
The spinning cube graphically displayed network traffic, especially malicious attempts to breach the network, captured from SCinet, the conference's network, using the Bro Intrusion Detection System. Bro was first developed by Vern Paxson of Lawrence Berkeley National Laboratory. Bro, which had been used at the conference since SC2000, was instrumental in detecting numerous compromised systems, malicious behavior and also for capturing and displaying clear text passwords.
Lau said he came up with the visual cube to better inform non-experts about issues in computer security. Until the cube came to be, such information was typically presented as text-based information.
“It was hard to understand what was going on, so it got me thinking about a way to show the information that was visually interesting and communicated useful information,” Lau said. “It really captured attention and people could quickly grasp what was going on in real-time.”
In his writeup about the project, Lau noted that “It is sometimes difficult for those unfamiliar with computer security to conceptualize the overall extent of malicious traffic on the Internet today. Unfortunately, it is often these very same people who are continual victims of computer security incidents.”
Unlike many institutions, SCinet operated as an open network, with monitoring rather than firewalls.“Since many of the attendees and exhibitors come from a network environment that has a firewall or filtering in place, they are often surprised at the swiftness that their systems are compromised on the ‘open’ Internet,” Lau continued.
To help educate attendees, SCinet used Bro to capture and then post clear-text passwords for all to see at the conference. “The reactions of many attendees who have seen this display, however, has been proof positive that there is a wide information gap between what non-computer security people believe is possible and what is considered to be "common knowledge" amongst computer security professionals. It is this information gap that the cube attempts to address,” Lau wrote.
Using the data collected by Bro, all TCP connections observed by Bro, both attempted and successful, are displayed as points in the cube. Each connection is a single point. The successful connections (SYN/FIN) are shown as white dots. The multi colored dots represents incomplete TCP connections, either SYN/RST or SYN with no response. The incomplete connections are colored using a rainbow colormap with the color varying by port number. This color mapping was used to assist the viewer in locating the point in 3D-space. The vast majority of colored dots can be considered to be malicious traffic searching for vulnerable systems.
Besides the primary educational aspect of the Cube, the secondary goal was to investigate new techniques in visually analyzing network traffic and also to develop a tool that would potentially assist those involved with computer security to visually "see" new forms of attacks, according to Lau.
The Spinning Cube not only captured the attention of SC03 attendees, but also reached a wider audience through an article (PDF | 75KB) Lau wrote for ACM Communications.
Upate: As of May 2015, the piece had been cited 172 times and Lau said he continues to get occasional inquiries about the project.
About NERSC and Berkeley Lab
The National Energy Research Scientific Computing Center (NERSC) is a U.S. Department of Energy Office of Science User Facility that serves as the primary high performance computing center for scientific research sponsored by the Office of Science. Located at Lawrence Berkeley National Laboratory, NERSC serves almost 10,000 scientists at national laboratories and universities researching a wide range of problems in climate, fusion energy, materials science, physics, chemistry, computational biology, and other disciplines. Berkeley Lab is a DOE national laboratory located in Berkeley, California. It conducts unclassified scientific research and is managed by the University of California for the U.S. Department of Energy. »Learn more about computing sciences at Berkeley Lab.







